46+ Listen von Arp-Spoofing: Arp spoofing, also called arp poisoning, is one such method that is used by hackers to intercept communications between two devices on the same local area network (lan) to exploit sensitive data.
Arp-Spoofing | This way you could control the traffic and also even stop it. The hacker tells the gateway that their mac address should now be associated with the target victim's ip address. Android & ios pokemon go! Em redes de computadores, arp spoofing (falsificação de arp), arp cache poisoning (envenenamento de cache arp) ou arp poison routing (roteamento de envenenamento de arp), é uma técnica pela qual um invasor envia mensagens (falsificadas) do address resolution protocol (arp) para uma rede local.geralmente, o objetivo é associar o endereço mac do atacante ao endereço ip de outro hospedeiro. Spoofing may denote sniffing out lan addresses on both wired and wireless lan networks. Hackers have always leveraged the arp protocol vulnerability to poison legitimate data transmission sessions since the protocol. We would first understand address resolution protocol and then perform an arp spoofing attack using arpspoof. This form of attack results in hackers sending out fake arp packets that slide in between two communicating systems unnoticed so they can listen to or manipulate their data traffic. Arp packets can be forged to send data to the attacker's machine. Arp spoofing is also known as arp poisoning, and occurs when malicious arp packets are sent to a default gateway on a lan. We would first understand address resolution protocol and then perform an arp spoofing attack using arpspoof. Em redes de computadores, arp spoofing (falsificação de arp), arp cache poisoning (envenenamento de cache arp) ou arp poison routing (roteamento de envenenamento de arp), é uma técnica pela qual um invasor envia mensagens (falsificadas) do address resolution protocol (arp) para uma rede local.geralmente, o objetivo é associar o endereço mac do atacante ao endereço ip de outro hospedeiro. You'll quickly fill your pokedex with our helpful guides that will get you spoofing quickly and safely in pokemon go! As a result, all the traffic that is meant for the victim will reach the attacker first. This way you could control the traffic and also even stop it. It can be understood with the help of the following points − first arp spoofing, for overloading the switch, will constructs a huge number of falsified arp request and reply packets. Answer all of your questions about pokemon go! As can be seen, from serial number 247, all the packets with source and destination addresses of 172.31.81.160 and 172.31.102.14 are going through my pc. Spoofing may denote sniffing out lan addresses on both wired and wireless lan networks. It's basically arp table poisoning. It is a technique that hackers use to gain access to a network to steal data packets that pass through the local network. This is done to alter the ip/mac address pairings in the arp table. You must provide the gateway and the host's ip address as command line arguments. Arp spoofing is a technique that allows an attacker to craft a fake arp packet that looks like it came from a different source, or has a fake mac address in it. It is used to allow the attacker access to incoming internet traffic on a lan by having their media access control. The hacker tells the gateway that their mac address should now be associated with the target victim's ip address. Security was not a paramount concern when arp was introduced in 1982, so the designers of the protocol never included authentication mechanisms to validate arp messages. It can be understood with the help of the following points − first arp spoofing, for overloading the switch, will constructs a huge number of falsified arp request and reply packets. Address resolution protocol (arp) spoofing is a technique that causes the redirection of network traffic to a hacker. The attack works as follows: This results in the linking of an attacker's mac address with the ip address of a legitimate computer or server on the network. Android & ios pokemon go! Arp is a communication protocol that is used to map/resolve dynamic internet protocol… Arp stands for address resolution protocol. An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. Then the switch will be set in forwarding mode. Another popular arp spoofing tool is arpspoof, the following is how to use this command to perform arp spoofing: Arpspoof is a preinstalled kali linux utility that lets you expropriate traffic to a machine of your choice from a switched lan. It is a technique that hackers use to gain access to a network to steal data packets that pass through the local network. Arp spoofing is a technique that allows an attacker to craft a fake arp packet that looks like it came from a different source, or has a fake mac address in it. Answer all of your questions about pokemon go! An arp spoofing, also known as arp poisoning, is a man in the middle (mitm) attack that allows attackers to intercept communication between network devices. I have never tested these, though. As a result, all the traffic that is meant for the victim will reach the attacker first. As can be seen, from serial number 247, all the packets with source and destination addresses of 172.31.81.160 and 172.31.102.14 are going through my pc. The switch is set in forwarding mode and after the arp table is flooded with spoofed arp responses, the attackers can sniff all network packets. Arp spoofing constructs a large number of forged arp request and reply packets to overload the switch. The attacker must have access to the network. In this article, we'll take a look at arp spoofing, or arp poisoning, what is it, how it works, how you can detect arp spoofing attacks and finally, how to prevent an attack on the arp protocol. Arp poisoning is also known as arp spoofing. This is done to alter the ip/mac address pairings in the arp table. The switch is set in forwarding mode and after the arp table is flooded with spoofed arp responses, the attackers can sniff all network packets. Address resolution protocol (arp) spoofing attack is a type of network attack where an attacker sends fake address resolution protocol (arp) messages inside a local area network (lan), with an aim to deviate and intercept network traffic. This is why arpspoof serves as the most accurate way to redirect traffic, practically letting you sniff traffic on the local network. In this article, we have elaborated in detail on arp and arp spoofing. A few sites claim to have windows executables. This is a simple implementation of an arp spoofing attack. Arp spoofing, also called arp poisoning, is one such method that is used by hackers to intercept communications between two devices on the same local area network (lan) to exploit sensitive data. As can be seen, from serial number 247, all the packets with source and destination addresses of 172.31.81.160 and 172.31.102.14 are going through my pc.
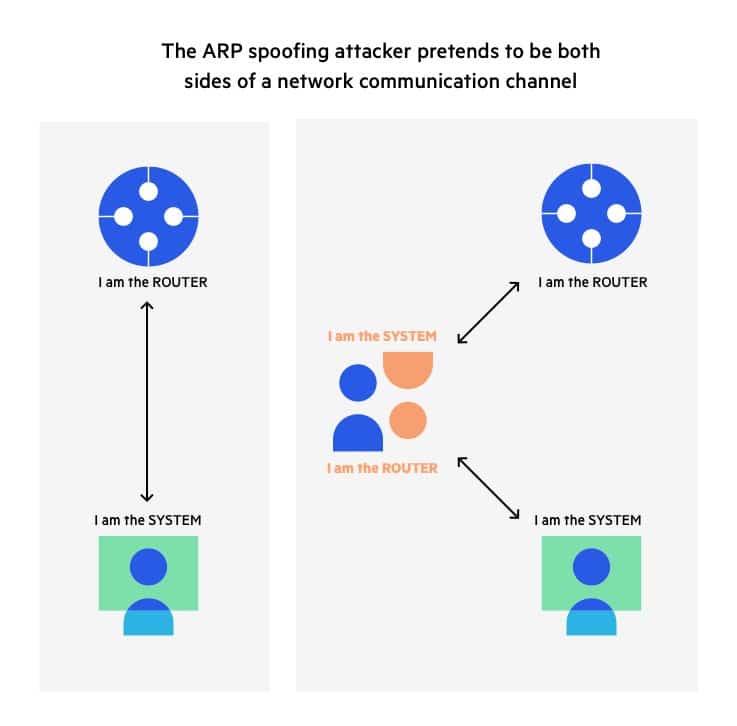

Arp-Spoofing: This way you could control the traffic and also even stop it.
0 comments :
Post a Comment